Wireless Penetration Test (WPA2)
Vulnerability Assessment/Penetration Testing
WPA2 Handshake Cracking
Introduction
What is Penetration Testing
Penetration testing also known as pen test and ethical hacking, is identified as a cybersecurity technique that organizations use in order to identify, test vulnerabilities and also highlight their security posture. These tests are typically performed by ethical hackers or also known as white hat hackers in which the employees or third parties of the company mimic the various strategies that an attacker performs, this is so the evaluation of the hackability of the organizations are, in addition the network and web applications of the organizations, moreover, the pen testing can be applied to test the adherence of their company regulations of their compliances (Mehta, 2018).
Ethical Hackers
Furthermore, Ethical hackers are the information technology experts who expertise in the methods of hacking to aid companies identify any possible vulnerability points inside their infrastructure, with the use of different methodologies, tools, techniques and approaches, the companies can test various simulated cyber-attack methods, in order to identify the strengths and weaknesses that are currently existing in their systems. There are various penetration testing strategies, involving different levels of expertise and the necessary information needed in order to carry out the attack, example, white box testing the attacker responsible for the penetration testing are given all the required information in order to carry out the penetration testing, black box penetration testers are given no information and have to carry out their necessary vulnerability assessment typically to identify the possible flaws, moreover, gray box testers are partially given knowledge about the system
Why is Penetration Testing Performed
Penetration testing is performed to evaluate a companies overall security infrastructure in which some companies may be strong and robust in a certain area but can be weak in other parts of their infrastructure, which is the reason why penetration testing is conducted.
Test Security Controls:
- Gaining the insights into the stability of the application, network and also physical security layers
Find Real-World Vulnerabilities:
- Used to expose the end points inside the computer systems that are most susceptible to attacks
Ensure Compliance:
- With the use of industry standards incorporated by penetration testing the companies can main their information security compliance
Reinforce Security Posture:
- Penetration testing ensure the companies by providing security program to address their vulnerabilities.
For the Vulnerability Assessment/Penetration testing to work efficiently, a wireless card is required. For this Penetration testing, the Wireless Card that will be used is a “Ralink WLAN Card” which is capable of being put into “Monitor Mode” that is used to capture data packet floating in the air space. Which is what will be used to crack the WPA2 network. Vulnerability Scanning is a necessity for this penetration testing as the required flaws are required to be analyzed in order to perform a successful penetration testing, the types of vulnerability that will be identified and analyzed will be the type of wireless encryption also the various ports, channels and strength of the WLAN, these are all required in order to obtain the optimal success of the penetration testing.

The next step is to check the state of the wireless card, whether it is in monitor mode or not. As seen in the image below, the wireless card is in fact in “Managed Mode” so it will require to be put into “Monitor Mode”
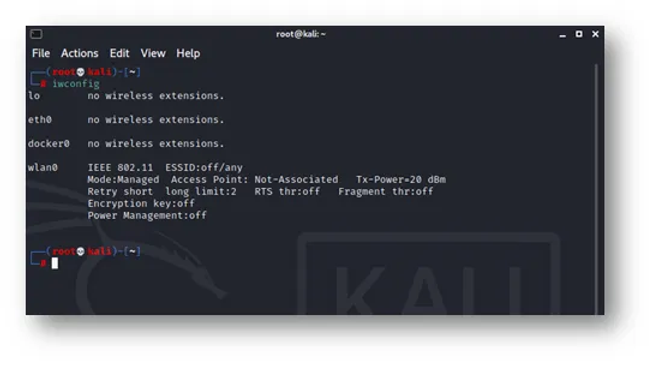
To put into “Monitor Mode” the following command is used;

- It also shows the running processes that are required to be terminated in order for the penetration testing to be successful. If these processes are not killed then it can interrupt monitor mode and potentially cause the wireless card to be put back into “managed mode”.
To terminate the process the command “kill” is used followed by the process identification number as seen below.
Additionally, the following can also be used to terminate running processes.
Proceeding to the vulnerability assessment phase. The tool that will be used is: airodump-ng. which is used to identify the WLAN encryption type, it displays the various channels, and also be able to show clients that are connected to the wireless access point. So, to begin
Using the command; airodump-ng wlan0mon will display all available access points.

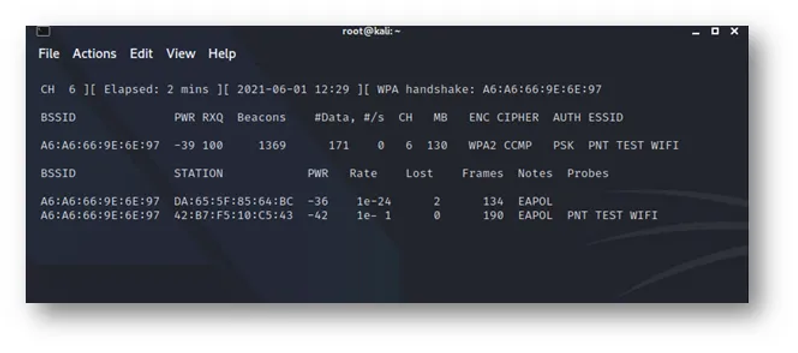
Shown below is the result of using the command: airodump-ng wlan0mon. Displayed are the available access points that have been captured with the help of monitor mode and the powerful tool; airodump-ng. From here on end as the pen tester, these information are critical to proceed to the penetration testing phase.

From the captured data, the important information that have been outlined are:

BSSID: Mac Address of the target Access Point
52:2F:1C:B8:5A:38
2. CH: Channel of which the access point is operating on: 6
3. ENC: The type of encryption that the Access point uses: WPA2
4. ESSID: Name of the Access point: PNT Test Wifi
To further view the vulnerability assessment about only the target AP, the command
airodump-ng -d (Mac Address of AP)
airodump-ng -d 52:2F: 1C:B8:5A:38
Once this information has been gathered, we can move on to perform the penetration testing.
Penetration Testing
To begin the penetration testing, the WPA handshake is required to be captured and to perform this can be a simple process and also a process that requires patience.
The simple gesture of it is de-authenticating the client from the access point, and once they tried to reconnect to the access point the handshake data will be captured and stored in a txt file that we will use to crack the WPA2 encryption password.
To begin:
The following command will be used:
Where:
-w: The file name of which the data captured will be stored
-c: the channel of which the access point is operating on
— bssid: the MAC address of the target access point
The following will be displayed, which will be waiting for the WPA 4-way handshake to appear, in this case as soon as the command was entered the handshake was captured

Typically, the ideal way to perform the handshake capture will be to use the command: aireplay-ng, which is used to deauth clients from the access point.
Below shows the command
aireplay-ng — deauth 0 -a A6:A6:66:9E:6E:97 wlan0mon
Where:
— deauth: The command used for de-authenticating
-a: The Mac Address of the target

After proceeding with the command, the following will be displayed, which shows the deauth commands being sent to the access point.

After some time, the WPA Handshake will be displayed that it has been captured, and here on end the handshake capture has been successful and can now proceed to the next step of the Penetration Testing.
Once this data has been captured, because we ran the command which saves the captured information into a text file, we will now have a look at exactly what type of information we captured.
So, to find out the captured data, simply open up a terminal and type
ls: To list the files

We can see the various folders and files that are contained withing that file, now if we look closer, we will see, some .cap file that has appeared. This is the exact file that we are looking for which contains the captured WPA2 handshake encryption information.
To view the contained files use:
wireshark (cap file)

Once the command has been inputted, the following window will be displayed. At first it may look complicated but for this pen test we are only interested about the WPA handshake information. To display this information, we need to input: eapol into the search bar to specify that we want to see only the handshake data.

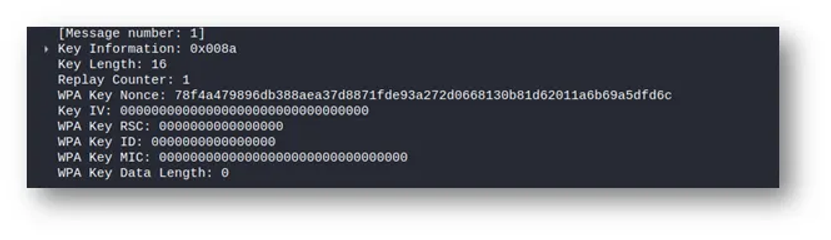
If we open up the various tabs that are located, we can dig deeper and identify even more information that has been captured, for example in the below image, we can see the WPA key nonce, which helps with the encryption of the access point.
Once all his information has been gathered, having access to the captured handshake cap file, we can now proceed to actually penetrating the access point. This will be a brute force attack with the use of a wordlists that is contain inside the kali linux machine. To initiate the attack the tool that is going to be used is: aircrack-ng
The complete command for the attack is:
Where:
PNTTEST-01.cap: is the captured handshake file name
-w: is the location of the wordlists that will be used (Locations may differ according to the wordlists.)
The following will be displayed once the command has been executed

Basically, the executions are basically, aircrack-ng trying its best to match the eapol data (handshake) with the wordlists and also with the WPA encryption information that are located within the handshake cap file. For this specific attack, aircrack-ng was able to crack the wpa2 password due to it being a very simple password: 12345678910. The password was also conveniently located within the used wordlists, which made the penetrating testing process much easier.
Vulnerabilities Detected/Solutions
From the vulnerability scanning and Penetration testing, the identified vulnerabilities of the network that has been identified are:
1) The Password
12345678910
This kind of password will be really easier for an attack to crack and be able to gain access to your wireless network, although it is a long password, it does not contain any letters, symbols or punctuation variety to be able to withstand an attack. Although it is a WPA2 encrypted wifi network, with a password like that it is very vulnerable to attackers. This attack was specifically designed to target clients on the network, where it requires the client to give out a handshake, which occurs when the clients connect to the network, these information are captured and we are able to then view the captured handshake which is used to crack the WPA2 password.
Solution:
To solve this issue is really simple, the best thing you can do is simply change the password of the WLAN, however making sure the password is a strong password that will be susceptible to wireless attack such as this one. A strong password is one that you can’t simply guess it or crack with a brute force attack. WAP and WPA2 both have encryption mechanisms that manages keys and encryption however it is still susceptible to attack such as this one. A proper password that is unique in all methods is the correct way to avoid these attacks also the recommendation will be to change password every once in a while, maybe at least once per 3 months, just to ensure the proper security of the wifi network. A proper password must contain every possible variable to ensure is confidentiality, so a password like “w4rr3n@23d3n!c3”. This type of password will be basically impossible for a handshake attack with wordlist to be able to crack it. So, it is recommended that this type of password is used.
How to make your password more secure

Above Figure: Examples of Strong Passwords
Above, are my recommendation that you could implement into the existing password, it doesn’t have to be very complex and long, but it is required to contain a necessity of different variables in order to ensure the protection of the Wireless Network.
Last updated